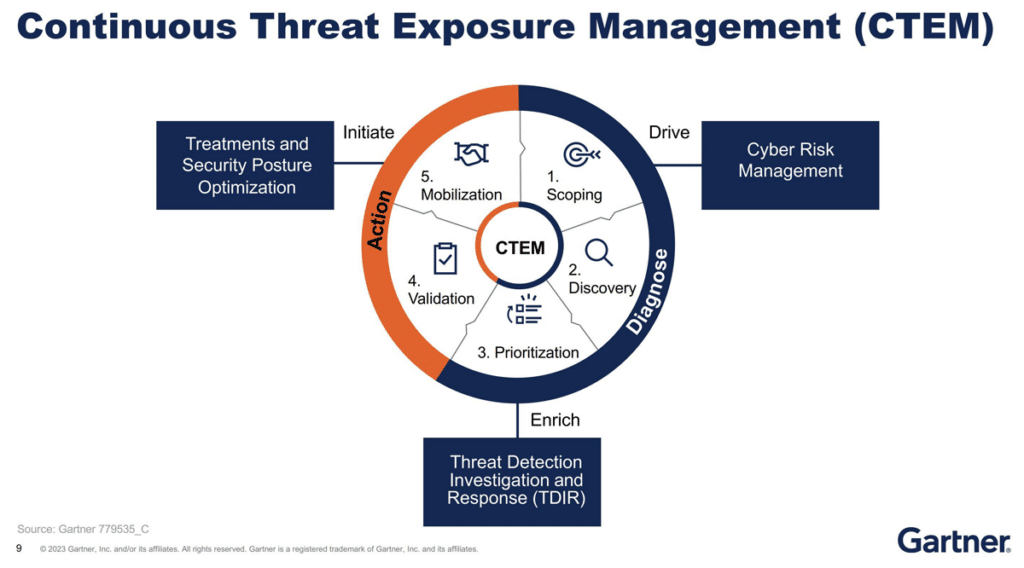
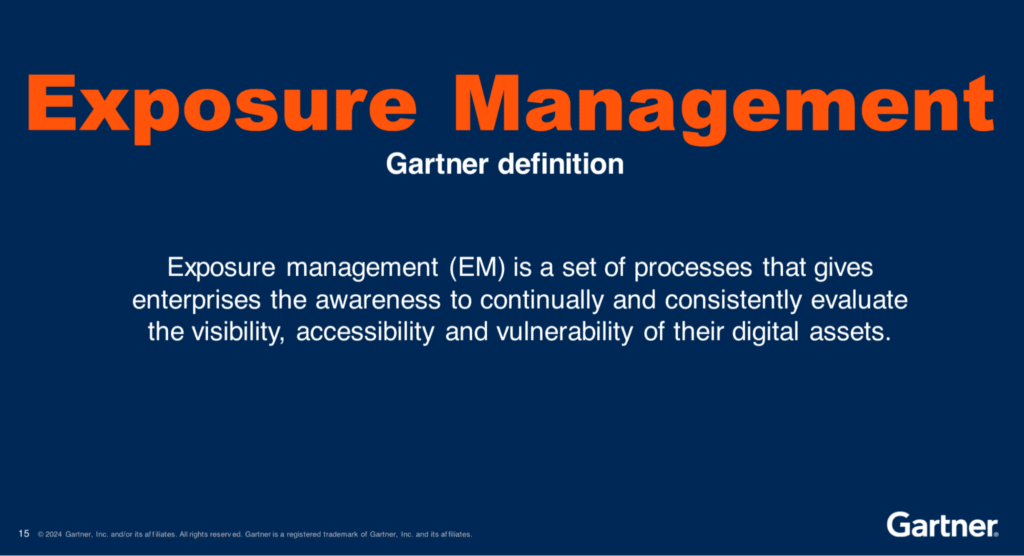
What is CTEM?
CTEM stands for Continuous Threat Exposure Management. It’s a cybersecurity approach that involves continuously monitoring and assessing an organization’s attack surface to identify and mitigate potential vulnerabilities.
Here’s a breakdown of what CTEM entails:
- Proactive approach: CTEM focuses on proactively identifying and addressing threats before they can be exploited.
- Continuous monitoring: It involves ongoing monitoring of an organization’s IT infrastructure, applications, and systems to detect changes and potential vulnerabilities.
- Risk assessment: CTEM helps organizations assess the risk associated with identified vulnerabilities and prioritize them based on their potential impact.
- Threat simulation: CTEM often involves simulating attacks to test an organization’s security posture and identify weaknesses.
- Exposure reduction: The goal of CTEM is to reduce an organization’s exposure to cyber threats by addressing vulnerabilities and improving security measures.
In essence, CTEM is a comprehensive approach to cybersecurity that helps organizations stay ahead of emerging threats and protect their valuable assets.
What are the stages of CTEM?
CTEM (Continuous Threat Exposure Management) involves a cyclical process of continuous monitoring, assessment, and remediation. While the specific stages can vary depending on the organization and the CTEM framework used, here’s a general overview of the common stages:
1. Scoping:
- Identify assets: This involves identifying all assets within the organization’s IT environment, including hardware, software, networks, and applications.
- Gather information: Collect detailed information about each asset, such as its location, purpose, and criticality.
2. Discovery
- Scan for vulnerabilities: Use vulnerability scanning tools to identify weaknesses in the organization’s systems.
3. Prioritization:
- Monitor threats: Keep track of emerging threats, vulnerabilities, and attack vectors.
- Analyze trends: Analyze threat intelligence to identify potential risks and trends.
- Prioritize vulnerabilities: Assess the risk associated with each vulnerability and prioritize them based on their potential impact.
4. Validation:
- Analyze attack surface: Evaluate the organization’s attack surface, which includes all points of potential entry for attackers.
- Identify gaps: Identify gaps in security controls and procedures that could be exploited.
5. Mobilization:
- Implement countermeasures: Develop and implement remediation strategies to address identified vulnerabilities.
- Monitor effectiveness: Continuously monitor the effectiveness of implemented countermeasures.
What are other important considerations in CTEM?
Reporting and Analytics
- Report on KPIs and SLAs: Track and benchmark risk and remediation performance.
- Manage risk exceptions: Continuously monitor and report risk exceptions, approval and oversight.
Continuous Monitoring and Improvement:
- Repeat the process: Regularly repeat the cycle of discovery, threat intelligence, vulnerability assessment, exposure assessment, and remediation to ensure ongoing protection.
- Refine processes: Continuously refine CTEM processes based on feedback and emerging threats.
It’s important to note that CTEM is an ongoing process, not a one-time event. Organizations need to continually adapt their CTEM strategies to address evolving threats and vulnerabilities.
What problem CTEM is solving?
CTEM (Continuous Threat Exposure Management) is designed to address the following key problems in cybersecurity:
- Proactive threat identification: Traditional security measures often focus on reactive responses to threats. CTEM aims to proactively identify potential vulnerabilities and risks before they can be exploited.
- Vulnerability management: CTEM helps organizations effectively manage vulnerabilities by identifying, assessing, and prioritizing them based on their potential impact.
- Risk mitigation: By understanding the risks associated with identified vulnerabilities, CTEM enables organizations to implement appropriate mitigation strategies and reduce their exposure to threats.
- Improved security posture: CTEM helps organizations strengthen their overall security posture by identifying and addressing weaknesses in their security controls and procedures.
- Compliance with regulations: CTEM can help organizations comply with various industry regulations and standards that require effective security measures.
In essence, CTEM is solving the problem of reactive security by providing a proactive and comprehensive approach to identifying, assessing, and mitigating cyber threats.
What does Gartner say about CTEM?
Gartner has been a strong proponent of Continuous Threat Exposure Management (CTEM), highlighting its importance in today’s evolving threat landscape. They have emphasized that CTEM is a crucial approach for organizations to effectively manage their attack surface and mitigate risks.
Here are some key points from Gartner’s research on CTEM:
- CTEM as a critical component of a mature security program: Gartner positions CTEM as a foundational element for organizations seeking to achieve a high level of security maturity.
- Benefits of CTEM: They have highlighted the numerous benefits of CTEM, including reduced risk exposure, improved incident response, and enhanced compliance.
CTEM as a response to evolving threats: Gartner has recognized the increasing complexity of cyber threats and the need for more proactive and continuous security measures. CTEM is seen as a solution to address these challenges. - Technological advancements supporting CTEM: They have also acknowledged the role of emerging technologies, such as artificial intelligence and machine learning, in enabling effective CTEM practices.
In summary, Gartner’s research has consistently emphasized the importance of CTEM as a strategic approach for organizations to enhance their cybersecurity posture and protect against evolving threats.
What are the differences between CTEM and RBVM?
CTEM (Continuous Threat Exposure Management) and RBVM (Risk-Based Vulnerability Management) are both cybersecurity frameworks designed to identify and mitigate vulnerabilities, but they have different approaches and focuses.
CTEM emphasizes a proactive and continuous approach to threat management. It involves:
- Continuous monitoring: Constantly assessing an organization’s attack surface for changes and vulnerabilities.
- Threat intelligence: Gathering and analyzing information about emerging threats to identify potential risks.
- Risk assessment: Evaluating the potential impact of vulnerabilities and prioritizing them accordingly.
- Remediation: Implementing measures to address identified vulnerabilities.
RBVM takes a risk-based approach to vulnerability management. It involves:
- Risk assessment: Prioritizing vulnerabilities based on their potential impact and likelihood of exploitation.
- Risk treatment: Developing and implementing strategies to mitigate identified risks.
- Periodic reviews: Regularly reassessing vulnerabilities and adjusting risk treatment strategies as needed.
Key Differences:
- Focus: CTEM focuses on continuous monitoring and proactive threat identification, while RBVM emphasizes risk-based prioritization and mitigation.
- Approach: CTEM takes a more comprehensive approach, encompassing threat intelligence, risk assessment, and remediation, while RBVM is more focused on risk management.
- Frequency: CTEM often involves continuous monitoring and assessment, while RBVM may involve periodic reviews based on risk levels.
In summary:
- CTEM is a proactive and comprehensive approach to threat management that emphasizes continuous monitoring and risk assessment.
- RBVM is a risk-based approach to vulnerability management that focuses on prioritizing and mitigating risks.
While both frameworks are valuable tools for improving cybersecurity, they have different strengths and may be more suitable for different organizations depending on their specific needs and priorities.
What are the differences between CTEM and CSPM?
CTEM (Continuous Threat Exposure Management) and CSPM (Cloud Security Posture Management) are both cybersecurity frameworks designed to improve an organization’s security posture, but they have different focuses and approaches.
CTEM is a more comprehensive approach that involves:
- Continuous monitoring: Constantly assessing an organization’s attack surface for changes and vulnerabilities.
- Threat intelligence: Gathering and analyzing information about emerging threats to identify potential risks.
- Risk assessment: Evaluating the potential impact of vulnerabilities and prioritizing them accordingly.
- Remediation: Implementing measures to address identified vulnerabilities.
CSPM is specifically focused on cloud security and involves:
- Inventory: Identifying and tracking all cloud resources and assets.
- Configuration assessment: Ensuring that cloud resources are configured according to security best practices.
- Compliance monitoring: Assessing compliance with relevant security standards and regulations.
- Vulnerability management: Identifying and addressing vulnerabilities in cloud environments.
Key Differences:
- Focus: CTEM is a broader framework that covers all aspects of threat management, while CSPM is specifically focused on cloud security.
- Scope: CTEM can be applied to any organization, regardless of its cloud usage, while CSPM is primarily relevant to organizations that rely heavily on cloud infrastructure.
- Tools: CTEM often involves a variety of tools, including vulnerability scanners, threat intelligence platforms, and security information and event management (SIEM) systems. CSPM typically involves specialized tools designed for cloud security, such as cloud security posture management (CSPM) platforms.
In summary:
- CTEM is a comprehensive approach to threat management that can be applied to any organization.
- CSPM is a specialized framework focused on cloud security that is particularly relevant to organizations that rely heavily on cloud infrastructure.
While both frameworks are valuable tools for improving cybersecurity, they have different strengths and may be more suitable for different organizations depending on their specific needs and priorities.
How to succeed in CTEM?
To succeed in Continuous Threat Exposure Management (CTEM), organizations need to adopt a comprehensive and systematic approach that involves the following key elements:
1. Strong Leadership and Commitment:
- Executive buy-in: Ensure that top-level executives are committed to CTEM and understand its importance.
- Allocate resources: Provide adequate resources, including budget, personnel, and technology, to support CTEM initiatives.
2. Comprehensive Risk Assessment:
- Identify assets: Conduct a thorough inventory of all assets within the organization’s IT environment.
- Assess vulnerabilities: Regularly assess the organization’s vulnerability landscape using appropriate tools and techniques.
- Prioritize risks: Evaluate the potential impact of identified vulnerabilities and prioritize them based on their risk level.
3. Effective Threat Intelligence:
- Monitor threats: Keep track of emerging threats, vulnerabilities, and attack vectors.
- Analyze trends: Analyze threat intelligence to identify potential risks and trends.
- Share information: Share threat intelligence with relevant stakeholders to facilitate informed decision-making.
4. Robust Security Controls:
- Implement countermeasures: Implement effective security controls, such as firewalls, intrusion detection systems, and access controls, to protect against threats.
- Monitor effectiveness: Continuously monitor the effectiveness of security controls and make necessary adjustments.
5. Continuous Monitoring and Improvement:
- Use advanced tools: Employ advanced tools and technologies to automate monitoring and detection processes.
- Review and refine: Regularly review and refine CTEM processes based on feedback and emerging threats.
- Foster a security culture: Promote a security-conscious culture within the organization, encouraging employees to report suspicious activities and follow best practices.
6. Collaboration and Partnerships:
- Engage with vendors: Collaborate with security vendors to stay updated on the latest threats and solutions.
- Partner with other organizations: Share best practices and lessons learned with other organizations in the industry.
By following these guidelines, organizations can effectively implement CTEM and significantly improve their cybersecurity posture.
How to choose a CTEM vendor?
Choosing the right CTEM (Continuous Threat Exposure Management) vendor is crucial for effectively protecting your organization’s assets and data. Here are some key factors to consider when making your decision:
1. Comprehensive Feature Set:
- Continuous monitoring: Ensure the vendor offers continuous monitoring of your attack surface for vulnerabilities and changes.
- Threat intelligence: Look for a vendor that provides access to up-to-date threat intelligence to help identify potential risks.
- Risk assessment: The vendor should be able to assess the risk associated with identified vulnerabilities and prioritize them accordingly.
- Remediation guidance: The vendor should offer guidance and support for implementing effective remediation strategies.
2. Scalability and Flexibility:
- Scalability: The vendor’s solution should be able to scale with your organization’s growth and changing needs.
- Flexibility: Consider the vendor’s ability to integrate with your existing security infrastructure and workflows.
3. Ease of Use:
- User-friendly interface: Look for a vendor that offers a user-friendly interface that is easy to navigate and understand.
- Minimal training requirements: The vendor’s solution should require minimal training for your team to use effectively.
4. Customer Support and Service:
- Responsive support: Ensure the vendor offers responsive and effective customer support.
- Service level agreements: Consider the vendor’s service level agreements to understand the level of support you can expect.
5. Cost and ROI:
- Pricing structure: Evaluate the vendor’s pricing structure to ensure it aligns with your budget.
- Return on investment: Consider the potential return on investment (ROI) of implementing the vendor’s CTEM solution.
6. Reputation and Experience:
- Industry reputation: Research the vendor’s reputation in the cybersecurity industry and look for customer reviews and testimonials.
- Experience: Consider the vendor’s experience in providing CTEM solutions and their track record of success.
7. Security and Compliance:
- Security certifications: Ensure the vendor has relevant security certifications to demonstrate their commitment to data protection.
- Compliance: Verify that the vendor’s solution complies with relevant industry regulations and standards.
By carefully evaluating these factors, you can choose a CTEM vendor that best meets your organization’s specific needs and helps you effectively protect your assets and data from cyber threats.